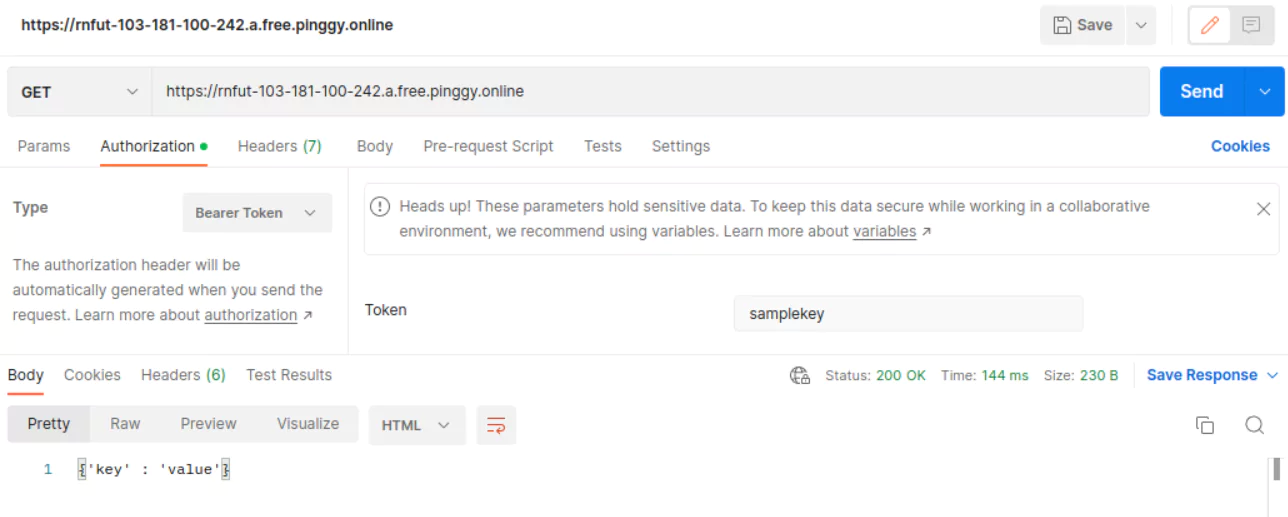
Key Authentication
Pinggy offers a mechanism for authenticating visitor connections using key-based authentication.
Key-based authentication involves visitors providing an ‘Authorization’ header with the value Bearer <key> with each request made. Pinggy provides the option to set a collection of keys during tunnel creation.
Start tunnel with key authentication as follows
ssh -p 443 -R0:localhost:<localport> -t a.pinggy.io k:key
ssh -p 443 -R0:localhost:<localport> -t <token>@a.pinggy.io k:key
Like basic authentication, one can set multiple keys as well.
ssh -p 443 -R0:localhost:<localport> -t a.pinggy.io k:key1 k:key2
ssh -p 443 -R0:localhost:<localport> -t <token>@a.pinggy.io k:key1 k:key2
You can customize the command here:
If you run the command with your specified port where your service is running, you will get an output similar to the following:
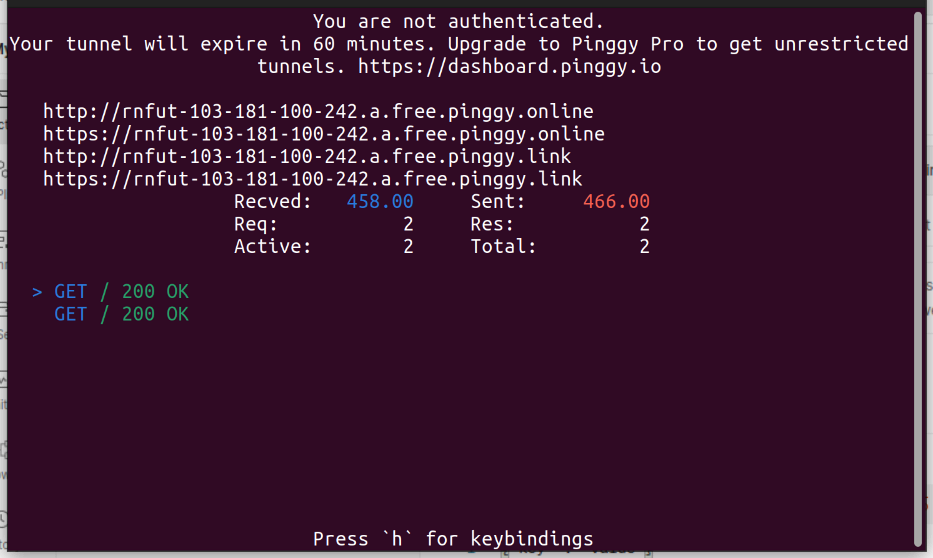
Here, you can see that the tunnel is authenticated with the key samplekey.